Introduction
Open proxies have traditionally been an IPv4 affair. Many abuse vectors (besides open proxies) have been tracked by organisations such as Spamhaus over the years, but it was only in 2011 that the organisation presented a strategic plan for how to even start adopting IPv6 into real-time blocklisting. Other abuse trackers such as DroneBL, Spamcop added IPv6 support to their stacks in the following years. Still, even back in 2016 when I conducted research for the Primer on Live Proxy Detection article IPv6 open proxies existed, but were viewed as a curiosity. As they were not seen as a prominent abuse vector in any of the Internet forums I was part of at the time they were omitted from my 2016 research.
However, a lot has changed over the past decade. IPv6 adoption and the number of prefixes have been growing at an exponential rate and the protocol has been well-supported by modern operating systems and new consumer equipment for years. As such, a fresh review of the state of IPv6 as an open proxy abuse vector was overdue, so I rewrote my open proxy detection stack in Q4 2023 to more effectively map out the IPv6 anonymisation space and start collecting trackable metrics.
Observations
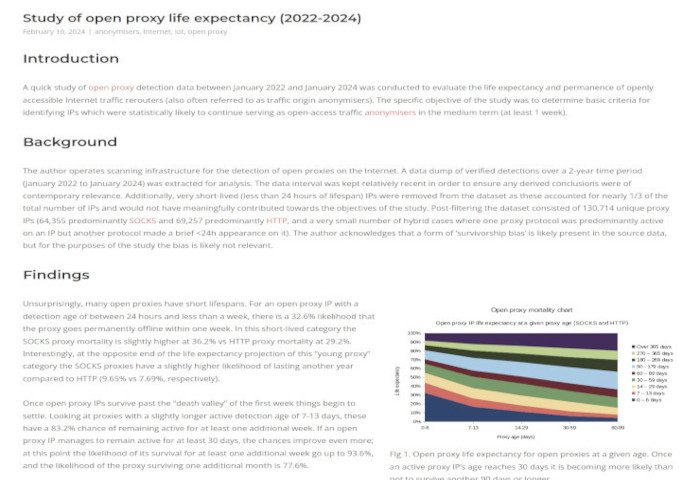
I expected a boring three-month study without any dramatic findings. Since early December 2023 the number of unique IPv6 open proxy exit IPs had shown a small but steady upward trend as shown in Figure 1 below, and although the total numbers weren’t very big compared to IPv4 it was still enough for me to keep going (aiming to eventually write some kind of post about the topic).
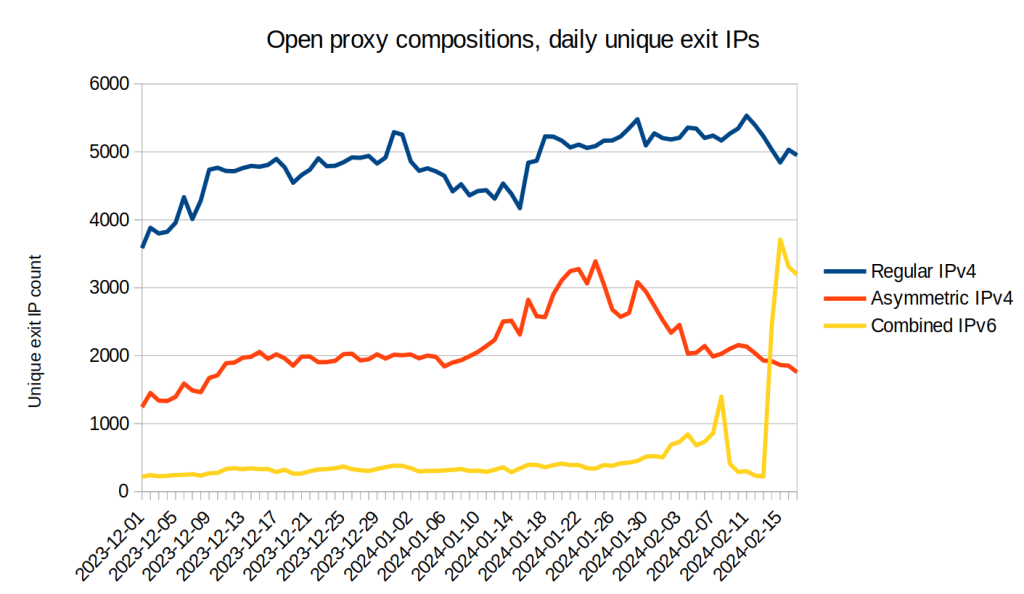
The average daily number of detected IPv6 exits in December 2023 were ca. 300, and in January 2024 the number had increased slightly to ca. 365, which was a modest (though likely not statistically significant) 22% increase. I expected to continue collecting additional data in order to confirm the trend line and wrap up the research as a “IPv6-capable proxies do exist, but are naught to worry about yet in terms of absolute numbers”-type piece. IPv4 detection rates had gone up by 15% between December and January as well so in relative terms the IPv6-to-IPv4 ratios had still only gone up by a paltry 0.24 percentage points (from 4.47% to 4.71%) so at the beginning of February this space didn’t look particularly interesting.
Then, just as I was wrapping up my article on Open Proxy Life Expectancy in early February the IPv6 proxy exit IP tracking statistics exploded (as seen in Figure 1) – all of a sudden the daily IPv6 exit numbers surged!
It wasn’t difficult to see what was happening – the new IPv6 proxy exit IPs were even visible in the Life Expectancy article’s complementary feed of semi-static open proxy IPs and all of this explosive growth stemmed from just a single /32 IPv6 net block belonging to a relatively new hosting company called Aeza International Ltd (as a group Aeza seems to have existed for a couple years, but the block belonged to a company that was incorporated in the UK as recently as September 2023 by a person listed as being resident in Kazakhstan).
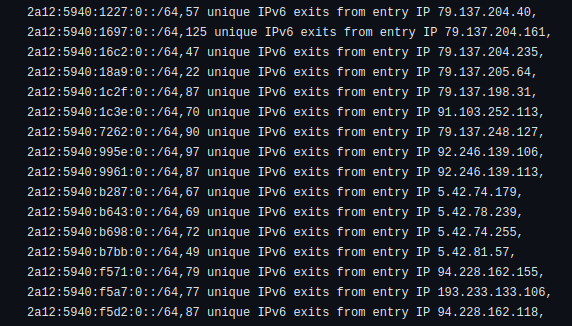
A quick look at Aeza’s website indicated that the company was offering VMs which included 1 IPv4 address and a full /48 IPv6 subnet per entry-level server, and evidently one or more operators had been setting up a growing number of open proxy servers on the Aeza network (with the IPv6 outbounds using many “random” unique /64 IPs bound to the allocated /48 subnets as per Fig 2 CSV output below).
Seeing such a dramatic change in the overall open proxy composition mid-study left me facing a dilemma. On one hand it would be scientifically more rigorous to keep running the study and only eventually post conclusions once all the facts were in, but on the other hand the Internet is a real-time dynamic system and news about changes to the status quo might immediately benefit people who deal with spam and other threats on a daily basis.
As such I decided to settle on a hybrid approach – I’m making the current (incomplete) findings public mid-study, but will continue amending the findings as I’m learning more. The fact at the time of writing this (February 18th 2024) is that 2a12:5940::/32 is spawning thousands of new unique IPv6 open proxy exits accessible to anyone on the Internet.
Update – March 17th 2024: The IPv6 open proxy composition has returned to January levels, so for now things are back to “normal”! I will let the study run its course and post final conclusions soon.
Final Update – January 2025: The Aeza spike proved to be an isolated incident rather than a trend. IPv6 open proxy numbers returned to baseline by late March 2024 and have remained there since – the daily IPv6 exit count has hovered around 350-400, roughly where it was before the February anomaly.
The underlying concern remains valid: the combination of cheap VMs and enormous IPv6 allocations means a motivated actor can spin up tens of thousands of unique exit IPs overnight. That it hasn’t become common practice yet is probably more about economics (IPv4 proxies still meet demand) than technical barriers. When that calculus shifts, subnet-level reputation tracking won’t be optional.
For now, the original recommendations stand. I’ll revisit if the landscape changes materially.
Conclusions
In summary, IPv6-enabled open proxies are here to stay, and due to the vastness of IPv6 space (with its generous per-customer prefix allocations) it must be assumed that subnet-level reputation tracking and blocking are becoming a necessity for effective mitigation of open proxy abuse vectors.
Although the Aeza open proxy incident may (hopefully) be a rare one-off for now, Aeza is likely not the last hosting company to allocate IPv6 /48s to entry-level virtual servers. The implication is straightforward – a /48 IPv6 subnet contains up to 1,208,925,819,614,629,174,706,176 unique IPs, and here they are all being routed to a single €5 per month VM. This is the new normal.
A few quick recommendations:
- If you use real-time blocklist polling make sure your queries are enabled for IPv6 – many old configurations may have originally been set up with IPv4-specific options.
- If you operate a blocklisting database, be sensitive to the fact that subnets as large as /48s are cheaper and more accessible than ever – and even being allocated to a single entry-level VM.
- For an up-to-date list of subnets with more-than-baseline IPv6 open proxy activity, my weekly CSV updates at https://github.com/mannfredcom/semi-static-proxy-ips/blob/main/proxy_subnets_7d_ipv6.csv might be useful. See the GitHub page for additional list options.